Our approach to protecting Information has always been focused on securing the digital assets that store, process, and transfer information. With increasing breaches, it is evident that our strategy is somehow solving half a piece of the puzzle and the other half related to the human factor is not considered seriously.
This is evident from the industry reports that Human error is the cause of nearly 95% of breaches. And some of the key factors that drive Human error are negligence, and lack of awareness which lead to data breaches.
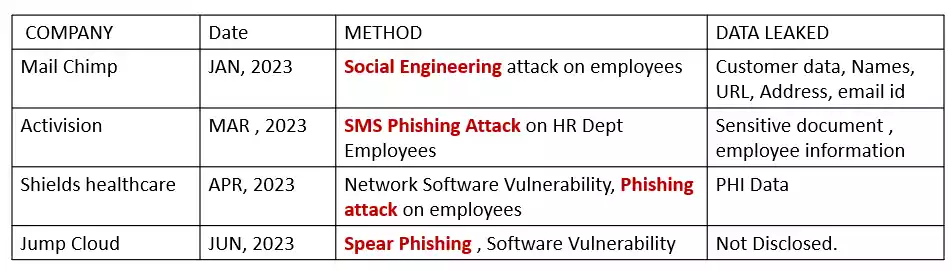
Lets review some of the major data breaches of 2023 , and attack methods used by Threat actors.

So, it’s evident that one of the most reliable attack vectors for Threat Actors is Social Engineering attacks like Phishing, Spear phishing, and Smishing attacks.
The risk owners have to clearly understand that solving the human risk is not just implementing a single control and or Checkbox Training and a quarterly Phishing simulation.
Transforming a Human Workforce into a self-resilient control requires a huge cultural change. This requires a continuous process-driven approach by engaging several Departments like HR and Cyber Security with support from Security Ambassadors in solving the Human risk problem.
The success of any program is defined by the clarity of its objectives and measurable metrics defining its progress. Similarly for managing the Human Risk, a successful process-driven approach is essential.
Let us evaluate the process designed by Intelliroot in Tackling the Human Risk.
![[Pasted image 20240515213954.png]]
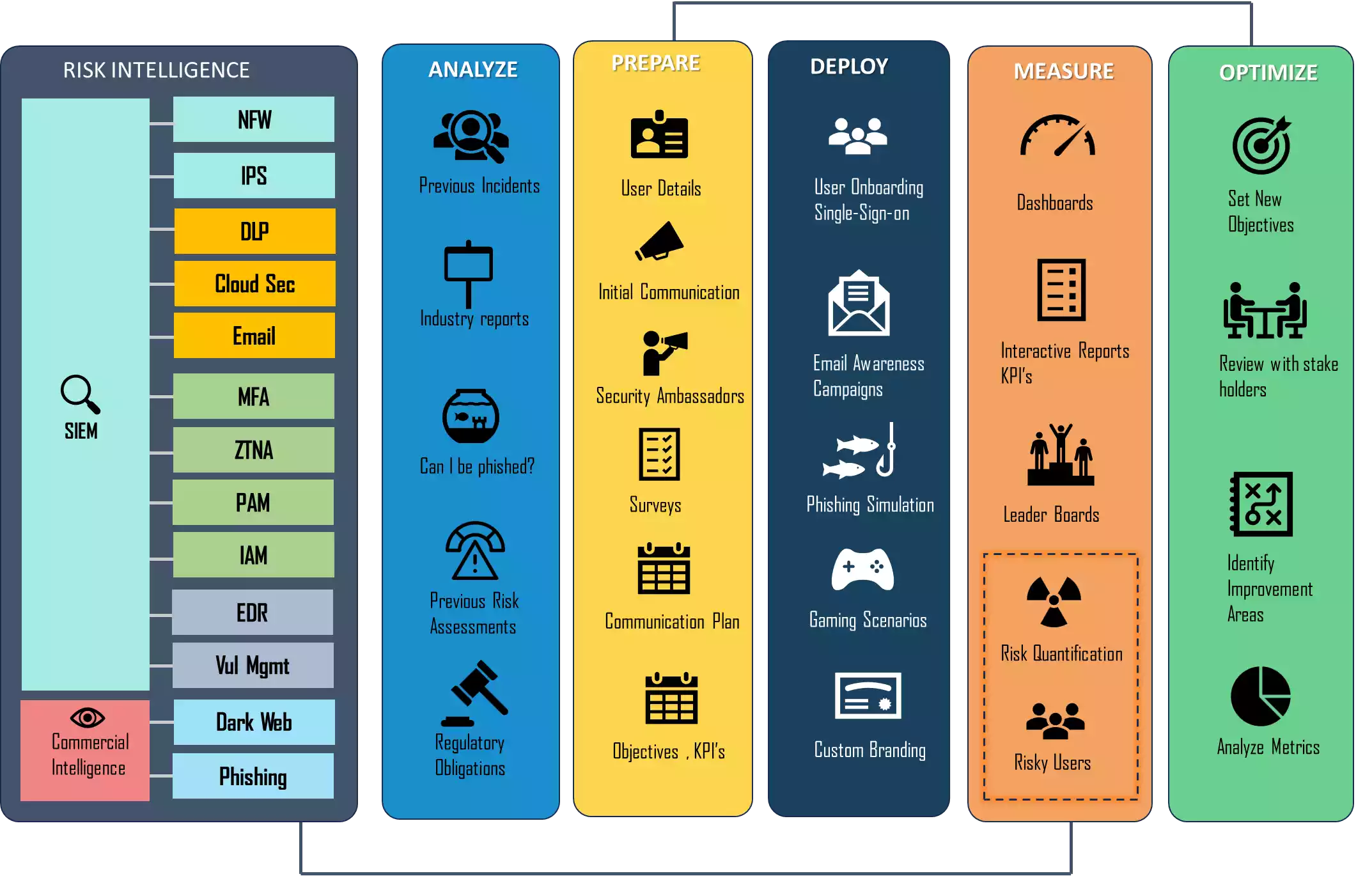
Analysis :
This is one of the critical phases that defines the roadmap of your complete program. This phase emphasizes understanding the current Cyber Security culture, the current Risks, and the regulatory and contractual obligations that you have to consider.
Prepare :
This phase emphasizes on identifying the objectives and preparing people, processes, and technology to drive your program.
Deploy
In this phase, we execute the plan established in the previous phases and engage with the users.
Measure
In this phase, we evaluate the performance of our program on the metrics defined based on our objectives. One important element of this phase is to execute the Rewards and recognition program to keep the users motivated.
Optimize
This phase is focused on understanding our strengths and weaknesses and setting new objectives to achieve them.
Building a cyber-resilient Human workforce is a continuous effort. Intelliroot's product INVINCIONE is a SaaS-based Human Risk management platform, that can help organizations to automate a lot of these efforts. It helps organizations build a process-driven approach to counter the modern threats targeting human assets.