In the vast landscape of the Internet of Things (IoT), communication protocols play a crucial role in enabling seamless connectivity. Zigbee, a wireless communication standard developed by the Zigbee Alliance, operates on the IEEE 802.15.4 radio frequency, specializing in low-power, short-range data transmission. Designed for applications in home automation, industrial control, and sensor networks, Zigbee stands out for its energy efficiency, scalability, and ability to form resilient mesh networks. Devices utilizing Zigbee can seamlessly communicate, forming interconnected networks that automatically adapt and self-heal. With its focus on minimizing power consumption and supporting a wide range of devices, Zigbee has gained prominence in the Internet of Things (IoT) ecosystem. Its flexibility makes it an ideal choice for smart home devices, facilitating reliable communication and contributing to the growth of interconnected and intelligent systems across various industries.
Zigbee offers two distinct security modes:
Distributed Security Mode: In the Distributed Security Mode with a unique Trust Center, there is no mandatory requirement for the network, and routers take on the responsibility of authenticating end devices. Devices come pre-configured with a link key, while the network key is assigned by a router upon joining the network. It's important to note that the network key remains constant for all nodes in the network, resulting in a relatively lower level of security compared to other modes.
Centralized Security Mode: Contrastingly, the Centralized Security Mode is employed in applications where a trust center plays a pivotal role in controlling and maintaining the centralized security policy for both the network and devices. Under this mode, the trust center assumes the following responsibilities: 1. Maintenance of security and security configurations for the entire network.
Authentication of devices and upkeep of a comprehensive list of devices connected to the network.
Management of both Link keys and Network keys, ensuring their distribution and association with all devices in the network.
Zigbee defines three types of devices:
ZigBee Coordinator (ZC): This device starts the network and selects the channel and PAN ID. It also communicates with routers and connects devices.
ZigBee Router (ZR): This device passes data between devices.
ZigBee End Device (ZED): This device is the one that will be controlled.
Types of ZigBee Security Key Network Key The first key on our list is the Network key, a vital component for a ZigBee network. This key is used to encrypt and decrypt data as it flies across your network, keeping your data safe and protected. Each device on your network is given a copy of this key, allowing them to verify the data packets they receive.
• The Network key is updated periodically for long-term security. • Stored securely in every device in the network.
Master Key Next comes the Master key, a shared secret between devices in a ZigBee network. It's used during the joining process when a new device is added to the network. The Master key helps establish an encrypted and authenticated channel between the new device and the Trust Center.
• It helps in safely adding new devices to the network. • Plays a crucial role in initial link security.
Trust Center Link Key Not to be forgotten is the Trust Center Link Key. This key is created during the process of joining a device to a network. It establishes a secure link between a device and the Trust Center, and plays a significant role in securing device management.
• Facilitates secure communication between devices and the Trust Center. • Essential for secure device management.
Application Key Finally, we have the Application Key, which encodes application data. This key is unique to each device and allows for personalized encryption and authentication, making it even more difficult for interlopers to access.
• Personalized encryption provides an additional security layer. • Ensures every device communicates securely.
Explanation of ZigBee encryption methods ZigBee utilizes the Advanced Encryption Standard (AES) 128-bit symmetric encryption. Encryption in ZigBee follows two steps:
In simple words, ZigBee AES encryption takes plaintext data, combines it with a secret key, and then transforms it into an unreadable text (ciphertext) - ensuring that the transmitted information could be accessed only by intended recipients.
ZigBee Network architecture
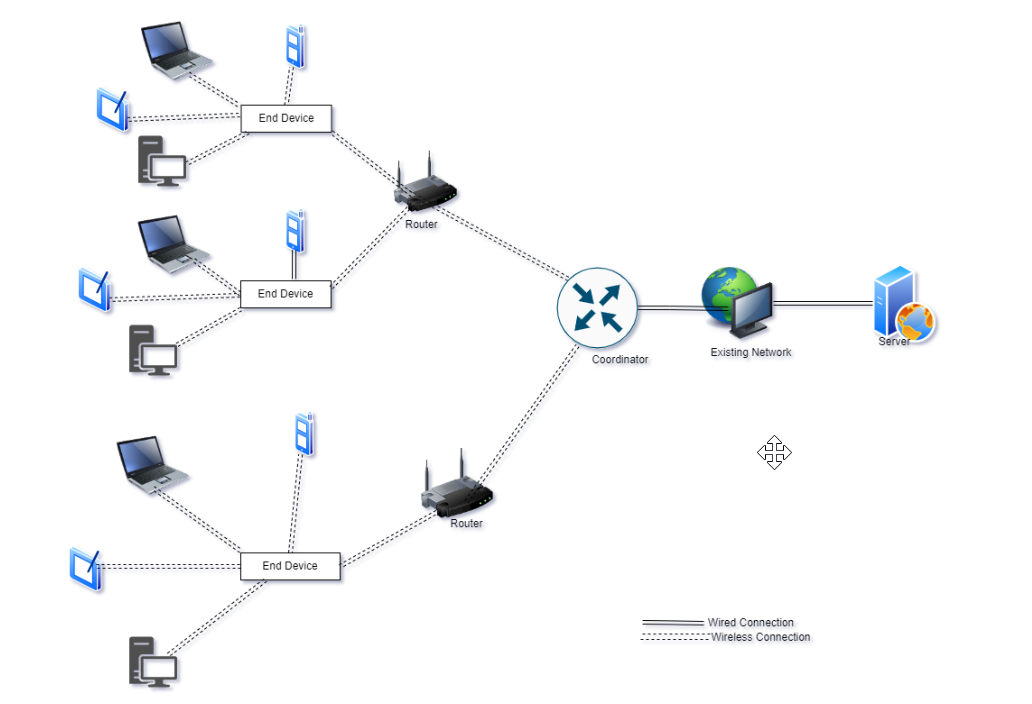
ZigBee networks function based on a mesh network architecture where each device, or 'node', can connect to multiple others within its range, creating multiple potential paths for data transmission. Unlike traditional hierarchical networks, this structure enables ZigBee networks to be incredibly resilient and flexible. If one device or pathway fails, data can be rerouted through another, ensuring consistent and reliable communication. This innovatively dynamic architecture makes ZigBee networks ideal for smart home systems.
• Mesh Network Structure: Interconnected device nodes, forming multiple data paths. • Resiliency: Data can be rerouted if a pathway fails. • Flexibility: Capable of adapting to changes and device additions.
Key Features:
Low Power Consumption: Zigbee devices are designed for energy efficiency, making them suitable for battery-powered applications with extended operational life.
Mesh Networking: Zigbee supports mesh networking, enabling devices to communicate through multiple paths, enhancing reliability and coverage in interconnected networks.
Security Features: Zigbee incorporates robust security measures, including encryption and authentication, ensuring secure communication and protection against unauthorized access.
Interoperability: Zigbee devices adhere to standardized profiles, fostering interoperability among products from different manufacturers and enabling diverse ecosystems.
Scalability: Zigbee networks can scale from small to large setups, accommodating varying numbers of devices and addressing the needs of different applications.
Applications of Zigbee
Smart Home Automation: Zigbee has found its niche in smart home applications. From smart lighting and thermostats to security systems and smart locks, Zigbee provides a robust and reliable communication framework for interconnected smart home devices.
Industrial IoT (IIoT): In the industrial landscape, Zigbee is making significant strides. Its ability to handle a large number of devices in a network, coupled with low power consumption, makes it suitable for industrial automation, asset tracking, and monitoring.
Healthcare and Wearables: Zigbee's low-power capabilities make it a viable option for healthcare applications, particularly in wearables and medical devices. It allows for continuous monitoring without draining the device's battery quickly.
Security Approach
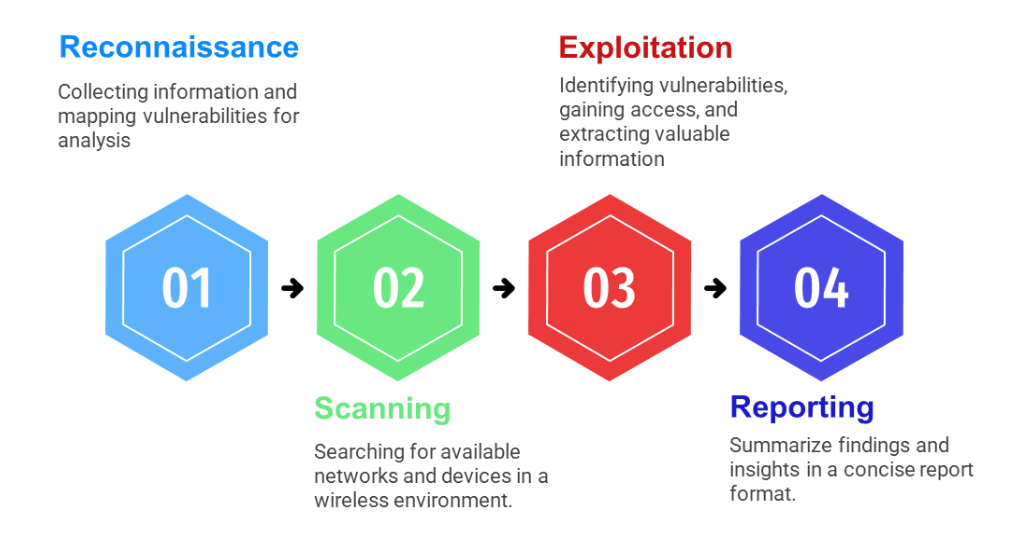
Vulnerabilities in ZigBee
Insecure Storage of Security Keys: The ZigBee protocol assumes that all security keys, including network and Link keys, are stored securely on devices. However, if not handled properly, these keys can be vulnerable to identification through reverse-engineering of the firmware binary. Securing the storage of keys is crucial to prevent unauthorized access through such reverse-engineering techniques.
Over-The-Air Insecure Key Transmission: Certain implementations pose a security risk during the initial integration of a node into a ZigBee network. In such instances, the node acquires its keys over-the-air, often in clear-text format from the coordinator. This approach exposes a potential vulnerability, as a network sniffer or rogue device can intercept these keys from the coordinator, posing a threat to the overall network security.
Energy Depletion Attacks: Two prevalent energy depletion attacks are noteworthy:
Invalid Security Header: Attackers send bursts of packets with invalid security headers, intending to force the targeted device to expend energy verifying frame integrity. This deliberate act accelerates the battery depletion of the target device, leaving it susceptible to compromise.
Polling Rate: In this attack, adversaries inundate the end device with packets at a rate surpassing the network's configured polling rate. This rapid influx of packets accelerates the energy consumption, leading to faster battery depletion of the target device. Vigilance against these energy depletion attacks is essential to maintain the resilience of ZigBee networks.
Network Jamming Vulnerability: While IEEE802.15.4/ZigBee standards incorporate protection mechanisms against radio and network interference, certain vulnerabilities exist, allowing attackers to employ jamming techniques. - Radio Jamming: In radio jamming attacks, the assailant amplifies the emission of the radio signal on a specific channel, causing a reduction in the Signal to Noise Ratio of the radio channel. This deliberate interference disrupts the normal functioning of the ZigBee network, potentially leading to connectivity issues and compromised communication.
Unauthenticated ACK Frame Vulnerability: While the Acknowledgment (ACK) frame is a crucial component of the network layer in IEEE 802.15.4/ZigBee standards, it is limited to confirming frame transmission without providing integrity and confidentiality protections for acknowledgment packets. This limitation opens the door to potential vulnerabilities.
ACK Spoofing: In ACK Spoofing attacks, assailants jam the network to prevent legitimate devices from receiving frames. Subsequently, the attacker sends a deceptive ACK frame with the correct sequence number to the sender. This deceptive action results in data loss within the ZigBee network, impacting its overall reliability and security.
ACK Dropping: ACK Dropping attacks involve the attacker jamming the network in a way that only the ACK frame from the receiver to the sender is affected. By disrupting this critical acknowledgment, the attacker forces the sender to repeatedly retransmit data until the maximum number of retransmissions is reached. This not only depletes the network bandwidth but also drains the battery power of the devices, leading to potential service disruptions and reduced operational efficiency. Vigilance against these ACK-related vulnerabilities is essential for maintaining the robustness of ZigBee networks.
Replay-Protection Vulnerability: While IEEE 802.15.4 incorporates replay-protection mechanisms, there exists a vulnerability that can be exploited by attackers,The standard's replay-protection feature dictates that a node can discard a received frame if its sequence number is equal to or less than the sequence number of the previously received frame from the same source node. In replay-protection attacks, a malicious actor can exploit this mechanism by sending frames with artificially inflated sequence numbers to the target node. Consequently, the target node, adhering to the replay-protection rule, drops frames with smaller, legitimate sequence numbers. This intentional manipulation compromises the integrity of data transmission, potentially leading to data loss, service disruptions, and security breaches within the IEEE 802.15.4 network. Ensuring robust countermeasures against such replay-protection vulnerabilities is essential for maintaining the overall security and reliability of the network.
Tools & Installation:
Best Practices for Managing ZigBee Security Keys
The management of Zigbee security keys is the most priority to ensure the protection of your smart home devices. Here are a few best practices:
• Do not share your network key with anyone you do not trust.
• Regularly update the security key, ideally every three months.
• Always use two-factor authentication whenever it’s provided.
• Always keep a backup of your key in a secure location.
In conclusion, Zigbee is more than just a wireless protocol; it's a driving force behind the seamless connectivity of IoT devices. As we move towards a more interconnected future, Zigbee stands tall, connecting the dots and powering the next wave of innovation in the Internet of Things.
Reference: https://en.wikipedia.org/wiki/IEEE_802.15.4

Learning from Real-World Phishing Attacks
August 13, 2024

RansomEXX targeting Indian Banks
August 2, 2024

The mutex vaccine for malwares
August 2, 2024

A pointer that brought the world to a standstill
July 21, 2024