Here is our new tool YARA_EDR. Well it’s not a full fledged EDR but it can call at a small part of an EDR to accurately detect malwares executing in your environment. The tool is a wrapper around the yara binary for windows. It relies on the memory scanning capabilities and scans the virtual memory of all the processes on a system to identify malware patterns. The detection is sent to Elastic search server along with information like user name and hostname.
The tool can be used for malware analysis, Threat Hunting, Incident Response. Let’s explore some features of the tool.
Yara has both File Scanning and Memory scanning capabilities. Let us talk in general about the features. Most of the antivirus have both the features. Both the features have pros and cons. While most yara rules are published in the context of File Scanning rather than memory scanning. As the name suggests File scanning scans the Files on the disk and Memory scanning scans the Virtual memory of the processes in the system. As mentioned YARAEDR relies on memory scanning.
If you look at the malwares today, we would say more than 90% of the malwares would be encrypted or packed. A single malware is distributed after packing them into various packers. Hence every file you collect for a single family of malware would look different from each other but behavior wise they are the same when they are executed. Hence it’s always a challenge for security analysts to find a common pattern in a file and write a signature that can detect all of the files belonging to the same malware.
But again when a malware is executed, the actual code of the malware unwinds itself into the memory. If you execute the variants belonging to a malware family, even though their files are different, there would be a lot of similarity in the code and strings found in the memory. YARAEDR tool takes the advantage of this point.
You would be questioning if Memory scanning is so effective why it is not used in all security products. In fact it is used in lots of malware detection products like antivirus, sandboxes, but memory scanning slows down the system drastically when it comes to scanning an endpoint. But there have been workarounds for the problem. Another great advantage of Memory scanning is accurately detecting malware.
The screenshot below shows the contents of file(left side) and memory(right side) of Snake keylogger malware.
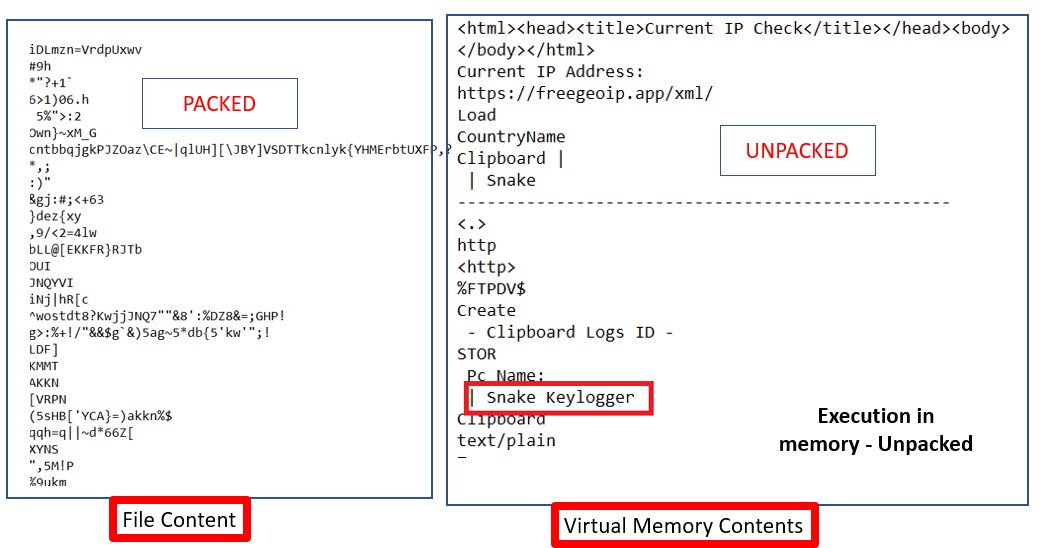
We often observe that same malwares are detected with different names by different security vendors. It’s a great thing that a threat is detected but at the same time, it’s also more important to detect it accurately.
It’s really important for a SOC team so that they can take the detection seriously. If a Ransomware which is a threat with high score is detected as an adware which is a low score threat, then the SOC team might not pay
much importance to that and as a result the Ransomware may compromise an entire organization. Similarly an advanced persistent attack that sits inside a network can be overlooked if the malware involved in the attack is
not detected accurately. A lot of APT group use RAT(Remote access Trojan) tools which might be specific to the group which if detected accurately, the group can be identified.
Most of the time Malwares are detected inaccurately as their the detections are based on the file content which might be packed or encrypted. Memory scanning has that advantage over File scanning.
While investigating huge sets of systems or threat hunting its important to correlate the information to identify patterns of the malware across systems. To facilitate this we have provisioned elasticsearch connectivity to this tool. This is will send the yara matched memory pattern to the Elasticsearch SIEM tool.
Tool can be used in Malware Analysis and Threat Hunting related scenarios. You can write malware signatures in form of yara rules and pass on to the tool.
There are two ways to use the program:
1. Python script
2. Standalone executable ( packed with Pyinstaller)
Option1 : Get help options
python yaraedr.py -h
yaraedr64.exe -h
Option2 : Use elasticsearch to forward logs and use single yara file
python yaraedr.py -es y -yf
yaraedr64.exe -es y -yf
Option3 : Use elasticsearch to forward logs and use directory with multiple yara files
python yaraedr.py -es y -yd
yaraedr64.exe -es y -yd